MFA Best Practices for ECU Users
All users configure Azure Multifactor Authentication* through their Microsoft 365 account when onboarding to ECU. Azure MFA allows log in to email, Canvas and other single sign-on applications.
For improved security protections, ECU recently turned on the account authentication (MFA) requirement for users both on and off campus without the “remember this device” option.
Recommended Best Practices
Follow these recommended best practices to ensure a smooth, secure experience when accessing the ECU resources you use every day.
Best Practice No. 1 – Make Microsoft Authenticator app your default sign-in method.
Once configured for your mobile phone or tablet (check app store for device compatibility), the access code can be used offline if network and cellular access is unavailable.
- Configure the Microsoft Authenticator app on a mobile device.
- Enable push notifications for Authenticator through your device’s settings.
Best Practice No. 2 – Configure multiple MFA methods.
If your mobile device is unavailable, you can use an alternate authentication method.
- Phone call. Set up a phone number to receive a voice call from Microsoft for authentication. You can add up to three different phone numbers.
- Click Add sign-in method to choose an alternate phone, office phone plus a mobile number from the Security info section of Microsoft 365.
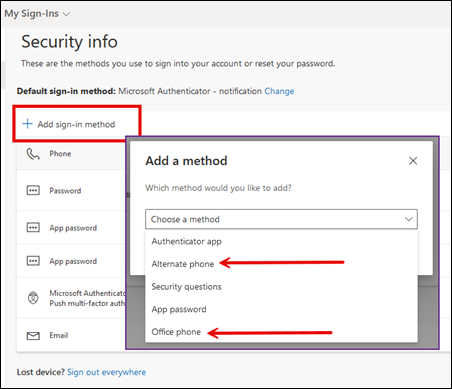
- Personal email. Add a non-ECU email address to receive the verification code.
Best Practice No. 3 – Work around weak cellular signals.
- Enable Wi-Fi calling to receive calls over the Wi-Fi network rather than cellular signals.
- See this information for onboarding your devices to eduroam, ECU’s primary Wi-Fi network.
- Use the Microsoft Authenticator app which can generate a verification code without an internet connection or cellular signal. The Authenticator app is the recommended default method for users.
Best Practice No. 4 – Periodically check app updates and verification settings.
- Regularly update the Microsoft Authenticator app to the latest version for improved security and features.
- Review and update your secondary authentication methods to ensure phone numbers and email addresses are up to date.
Best Practice No. 5 – Follow these security tips.
- Do Not Share Codes. Never share your verification codes with anyone.
- Do not approve an unexpected MFA prompt until you check your recent activity.
- Check your account’s recent activity through the Microsoft 365 My Sign-ins page. Ignore unsuccessful attempts, but a successful sign-in from a location you don’t recognize should be reported to the IT Service Desk.
Best Practice No. 6 – Contact Pirate Techs for questions and support.
- Call the IT Service Desk at 252-328-9866.
- Visit your nearest Pirate Techs walk-in location.
*I configured MFA twice when onboarding. What’s the difference?
- Azure MFA is used to log in to ECU resources and applies to these best practices.
- PirateID Self Service authentication is used for that system only to reset/unlock your password.
Post expires at 2:36pm on Friday February 28th, 2025
