Tips on How to Protect Yourself from Online Identity Theft and Phishing Scams
View the Adobe Spark version of this newsletter.
Cyber crime in all its many forms can, at best, wreak havoc in victims’ lives through major inconvenience and annoyance. At worst, cyber crime can lead to financial ruin and potentially threaten a victim’s reputation and personal safety.
While ITCS has taken many proactive steps to protect the university’s IT infrastructure, we want to help you keep your information and devices secure even when you’re not on campus or at work.
In this edition of the IT Security Series, we share tips and resources you can use to protect yourself from Online Identity Theft and Phishing Scams.
HOW TO PROTECT YOURSELF FROM ONLINE IDENTITY THEFT
Identity theft happens when someone steals your personal information to commit fraud. The identity thief may use your information to apply for credit, file taxes, or get medical services. These acts can damage your credit status, and cost you time and money to restore your good name.
Here’s what you can do to stay ahead of identity thieves:
Change your passphrases often for all online accounts. Generate a secure, unique passphrase for each separate account. Research different passphrase manager services* to find one that works best for you: NordPass, Keeper, RoboForm, Dashlane, and 1Password. If you’re uncomfortable storing your passphrases with a third-party cloud provider, there are passphrase managers such as the award-winning KeePass Password Safe that allow you to store them in your own secure location, through an encrypted database locked with a master key.
Your ECU passphrase must be changed every 90 days. Set your passphrase or texting number, change your security questions, unlock your PirateID, or change your notification email address through the Passphrase Maintenance page.
Note: If your ECU passphrase is changed while off campus (NOT connected to the ECU network), your ECU-managed desktop or laptop computer will not recognize the new passphrase. This means that when you log in to your computer, you must use the previous passphrase and use the new passphrase to log in to all other ECU systems. The fix for this problem is to connect to the ECU network through the virtual private network. Read more about resetting your ECU passphrase while off campus…
* Passphrase manager services are not officially endorsed or technically supported by ITCS.
Don’t save passphrases to websites or credit card information online. To minimize the potential damage of an attacker gaining  access to your credit card information, consider opening a credit card account for use only online. Keep a minimum credit line on the account to limit the amount of charges an attacker can accumulate.
access to your credit card information, consider opening a credit card account for use only online. Keep a minimum credit line on the account to limit the amount of charges an attacker can accumulate.
Avoid using debit cards for online purchases or when eating at restaurants (when your card may be momentarily out-of-sight). Credit cards usually offer some protection against identity theft and may limit the monetary amount you will be responsible for paying. Debit cards, however, do not offer that protection. Because the charges are immediately deducted from your account, an attacker who obtains your account information may empty your bank account before you even realize it.
How can you tell if someone has stolen your information? Some warning signs include:
- unfamiliar withdrawals from your bank account,
- unexplained medical provider bills for services you didn’t use,
- notification from the IRS that more than one tax return was filed in your name, or that you have income from an employer you don’t work for, and
- calls from debt collectors about debts that aren’t yours.
Report Identity Theft and Next Steps
HOW TO PROTECT YOURSELF FROM PHISHING SCAMS
‘Phishing’ is the term used to describe a cyber attack in which a carefully designed digital message or link is sent to fool someone into clicking on the link. When the individual does, it can either install malware onto the victim’s system or expose personal or sensitive data.
Phishing has been around for a while. The biggest change is the perpetrators are now much more sophisticated with their “bait.”
Following are steps you can take to protect yourself from phishing attacks:
Keep your software up-to-date. This includes our security software, your web browser, and your operating system. Those three are absolutely critical for keeping you and your information safe! Enable auto-update and check your programs’ Settings; the option is usually in there to automatically download new updates whenever one’s available.
Enable and use Multifactor Authentication (MFA). MFA, sometimes referred to as two-factor authentication or 2FA, is a security enhancement that allows you to present two pieces of evidence – your credentials – when logging in to an account. You already use it in some form. For example, you use MFA with your ECU email account.
You’ve also probably used MFA when you’ve swiped your bank card at the ATM and then entered your PIN (personal identification number), or logged into a website that sent a numeric code to your phone, which you then entered to gain access to your account.
Use your email spam filters. Your ECU email is protected through the Microsoft Exchange Online Protection’s spam filter that screens and quarantines suspicious email before it reaches your inbox. Spam is sent to the Outlook Junk folder. Considering current unfortunate geopolitical events*, ECU recently enabled additional email safeguards for the campus community.
Don’t respond to any suspicious or urgent messages requesting that you click a link, send money, or share sensitive information. If you receive a suspected malicious (phishing) email, forward the message to phish@ecu.edu or report a security concern to ITCS. We will analyze the email, and if it’s malicious, remove it from all users’ mailboxes. See this article on how to recognize phishing email from the Federal Trade Commission.
* Read the March 21, 2022 Statement by President Biden on our Nation’s Cybersecurity (The White House Briefing Room)
Examples of Phishing:
According to Norton Labs, tech support hoaxes topped the list of phishing threats from July 1 – September 30, 2021. Tech-support scams often arrive as a pop-up on your computer. They’re designed to trick you into believing you face a dire cybersecurity threat. Example: “Your PC is at risk!” They seek to steal your personal information, tap your bank account, or install dangerous software on your device. They capitalize on fear, uncertainty, and doubt. Never call a phone number based on a pop-up notification or warning. Instead, contact the company directly through its official website.
How to Avoid a Tech Support Scam / Federal Trade Commission: https://youtu.be/THYmUx3ofJk
In gift card scams, attackers use a website to try to guess gift card numbers and PINs until they find the right combinations. Then, they resell the cards online. With this scam, Norton advises people to always check the value of a gift card after you obtain it.
Additional steps to take:
- Inspect gift cards before you buy. A gift card should have all its protective stickers in place. Report the card to the store if anything looks scratched off or damaged.
- When you buy, save the receipt. Keeping the gift card receipt can be helpful if you run into problems with the card. If you are
 giving the gift card to someone else, attach the receipt to the card.
giving the gift card to someone else, attach the receipt to the card. - Treat gift cards like cash. Report a lost or stolen gift card to the card’s issuer immediately. Most card issuers have toll-free numbers you can find online to report a lost or stolen card. Depending on the card issuer, you may even be able to get some money back.
- Buy gift cards from sources you know and trust. Think twice about buying gift cards from online auction sites, to avoid buying fake or stolen cards.
Then there’s ‘Vishing,’ also known as voice phishing, which occurs when a criminal attempts to obtain valuable information or influence action via the telephone.
Attackers may call from a spoofed, blocked, or private phone number and ask for information such as:
- email addresses,
- home addresses,
- social security numbers, or
- user credentials for banks, email accounts, personal computers, etc.
Malicious callers often employ manipulative tactics to trick their targets into giving away sensitive information.
According to TechRepublic, COVID-19 contact tracing and testing scams and auto warranty calls dominated the landscape for 2020 and 2021.
How can you check to see if your email or phone number has been in a data breach?
(haveibeenpwned.com is a website that checks if an account has been compromised.)
‘Smishing’ is an attempt to collect logins or other sensitive information with a malicious text message—and it’s on the rise.
Threat ‘actors’ understand that consumers trust mobile messaging and they are much more apt to read and access links/URLs contained in mobile messages than those in email.
According to Proofpoint’s 2022 State of the Phish Report, reports of SMS/text (smishing), voice phishing (vishing), and social media-based attacks all increased by more than 20% in 2021.
A few ways to avoid vishing and smishing:
Add your phone number(s) to the National Do Not Call Registry. While the Do Not Call list is not foolproof, it should dramatically cut down on unwanted calls and text messages.
When you receive a spam text message on your phone, forward that text to the short code 7726 (which spells “SPAM”). You’ll 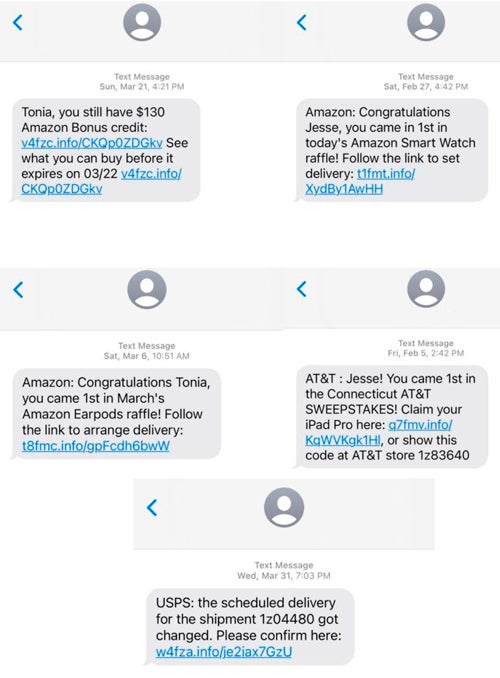 receive an automated message from your wireless carrier asking you to enter the phone number from which the spam text was sent. You can also report to the Federal Trade Commission (FTC) via website or 1-888-382-1222.
receive an automated message from your wireless carrier asking you to enter the phone number from which the spam text was sent. You can also report to the Federal Trade Commission (FTC) via website or 1-888-382-1222.
After reporting spam be sure to block the number through your wireless provider’s tools or services (check ctia.org, a website for the wireless industry, to learn about the options from different providers), or block phone numbers directly on your iPhone, iPad, or iPod touch or Android device.
Don’t click links sent to you via text message, unless you’ve been expecting them or have verified the sender is legitimate.
Visit trusted vendor websites directly (separately from text messages). If you receive a text message that asks you to take an action such as checking an order status or changing a password type—don’t click the link. Instead, type the organization’s URL directly into your browser and proceed from there.
Don’t respond to strange texts. Doing so only lets them know you’re a “real person,” setting you up for additional harassment down the road.
Examples of Vishing and Smishing:
Texts from banks, investment firms, and other financial institutions stating there’s an issue with your account.
Messages promising free money, products, or services.
Text messages from companies and service providers stating there’s an issue and you need to update your payment account information.
For more information, visit the websites below, the ITCS website, or contact Pirate Techs at (local) 252-328-9866 or (toll free) 800-340-7081.
- Information Security for Personally-Owned Computers (ECU)
- Information Security Standards and Best Practices (ECU)
- Security Awareness Education at ECU (ECU)
- Learn tips for protecting your computer, the risk of peer-to-peer systems, the latest e-scams and warnings, and Internet fraud schemes (FBI, Scams and Safety on the Internet)
- Protect your personal information from identity theft (FTC Consumer Advice)
- Learn more about the latest consumer advice and scams — and what you can do to protect yourself (FTC Consumer Advice)
- Learn how to protect yourself from and respond to scams and frauds (USA.gov)
We want to provide you with the most relevant and engaging information about ECU’s information technology services, tools, and resources. What topics would you like to hear about most?
